Docker Image Scan results for ibmcom/elasticsearch-ppc64le
Scan performed at 2022-12-12 15:23:07 using the CoGuard CLI
Summary
27 Total failed checks.
18 High / 3 Medium / 6 Low.
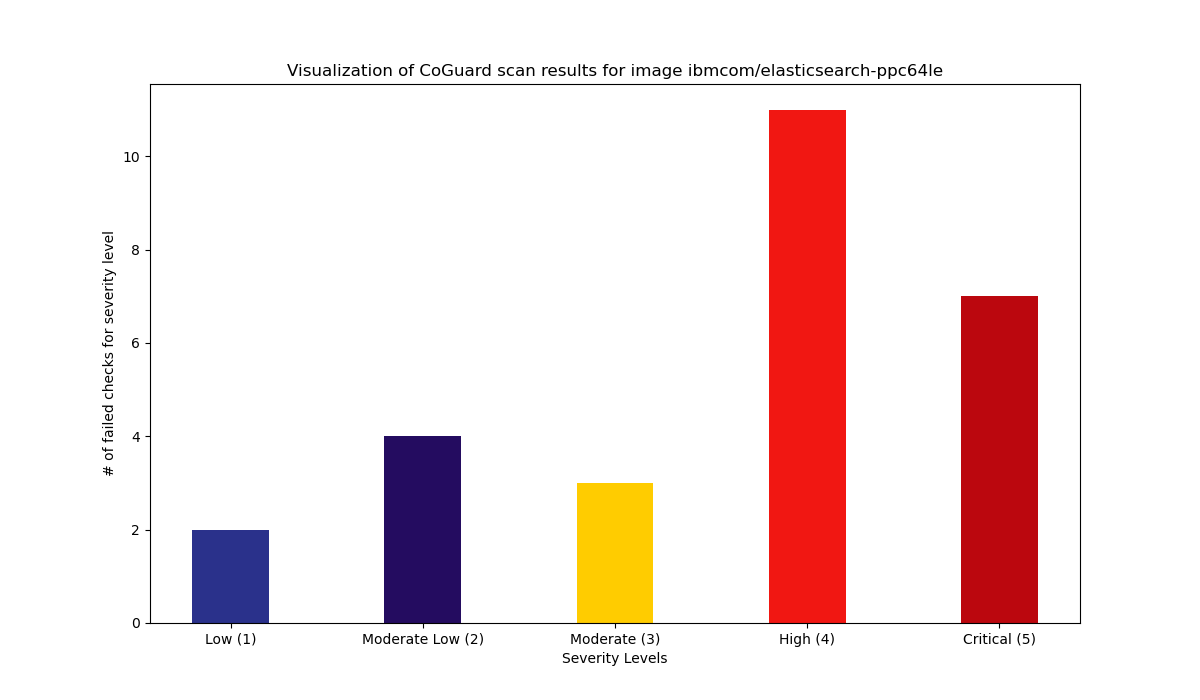
Details
| Rule identifier | Severity | Documentation |
|---|---|---|
| elasticsearch_filter_http_ip_addresses | 5 | ElasticSearch allows for black/whitelisting of IP addresses to connect to the cluster. This should be part of the consideration when setting up the cluster. Remediation: Ensure that the setting xpack.security.http.filter.enabled is true(default), that the key xpack.security.http.filter.allow has at least one value and that xpack.security.http.filter.deny is set to _all.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| elasticsearch_ssl_transport_enabled | 5 | ElasticSearch has by default transport SSL/TLS disabled. This should be enabled. Remediation: Ensure the setting xpack.security.transport.ssl.enabled is set to true (default false).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| elasticsearch_filter_transport_ip_addresses | 5 | ElasticSearch allows for black/whitelisting of IP addresses to connect to the cluster. This should be part of the consideration when setting up the cluster. Remediation: Ensure that the setting xpack.security.transport.filter.enabled is true(default), that the key xpack.security.transport.filter.allow has at least one value and that xpack.security.transport.filter.deny is set to _all.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| elasticsearch_encrypt_sensitive_data | 5 | ElasticSearch has a feature to allow for watchers to be enabled, which can alarm sysadmins if there are bad conditions met on the cluster. One can ensure that sensitive data is encrypted in the watcher, which should be done. Remediation: Ensure the setting xpack.watcher.encrypt_sensitive_data is set to true (default false) and xpack.watcher.encryption_key is pointing to a file containing the encryption key.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/notification-settings.html |
| elasticsearch_whitelist_http_connections | 5 | ElasticSearch has a capability to explicitly whitelist http connections. This should generally be done to control where traffic is allowed to come from to connect to the cluster. Remediation: Ensure that the key xpack.http.whitelist is set to a value other than * (default).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/notification-settings.html |
| elasticsearch_ssl_enabled | 5 | ElasticSearch has by default SSL/TLS disabled. This should be enabled. Remediation: Ensure the setting xpack.security.http.ssl.enabled is set to true (default false).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| elasticsearch_security_enabled | 5 | ElasticSearch has a setting to enable and disable security features. Depending on the license, the default is enabled or disabled. Hence, it is advisable to explicitly set this setting to true.Remediation: Ensure the setting xpack.security.enabled is set to true explicitly (ambiguous default).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| elasticsearch_no_default_ports | 4 | As a general best practice, default ports for a service should not be used, since it makes discovery harder for an attacker. Remediation: Set http.port to any port range other than 9200-9300Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/modules-http.html |
| elasticsearch_ssl_supported_protocols_secure | 4 | ElasticSearch should use secure transport SSL protocols, which are nowadays TLSv1.2 or higher. Remediation: Ensure that the key xpack.security.transport.ssl.supported_protocols does not contain any protocols older than TLSv1.2 (default value is TLSv1.2,TLSv1.1).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html#ssl-tls-setting |
| elasticsearch_ssl_supported_http_protocols_secure | 4 | ElasticSearch should use secure http ssl protocols, which are nowadays TLSv1.2 or higher. Remediation: Ensure that the key xpack.security.http.ssl.supported_protocols does not contain any protocols older than TLSv1.2 (default value is TLSv1.2,TLSv1.1).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html#http-tls-ssl-settings |
| dockerfile_last_user_should_be_non_root | 4 | When creating a Docker container, it is possible to set the user who is actually running the application and any command on the container. It is important to specifically use the USER directive in any Dockerfile to ensure that the user is not root and has unnecessary privileges. Remediation: Have at least one USER directive in your Dockerfile, and the last user directive should not reference the root user or root group. Source: https://docs.docker.com/engine/reference/builder/#user |
| elasticsearch_authc_token_enabled | 4 | ElasticSearch's built-in token service has ambiguous default settings, and it is recommended to explicitly set it to true. Remark: We assume that xpack.security.http.ssl.enabled is set to true, which is checked by a different rule.Remediation: Set the key xpack.security.authc.token.enabled to true explicitly.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| elasticsearch_disable_http_compression | 4 | Compression of http traffic helps with performance, but comes at the cost of an attack vector known as the BREACH-attack. Hence, for security purposes, it is recommendable to turn compression off. Remediation: Set the value of http.compression to false explicitly (there is some more complex logic involved for the default value, so setting it explicitly is recommended).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/modules-http.html |
| elasticsearch_allow_monitoring | 4 | ElasticSearch is regularly used to collect monitoring data from e.g. LogStash, Kibana, or Beats. There is a setting to ignore the collection from these sources, which is the default behavior. It is advisable to keep this on. Remediation: Ensure that the setting xpack.monitoring.collection.enabled is set to true.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/monitoring-settings.html |
| elasticsearch_ensure_audit_enabled | 4 | It is an important security best practice to audit events like authentication failures, refused connections and data-access events. Remediation: Set the setting xpack.security.audit.enabled to true (default is false).Remark: Auditing security is only available for certain ElasticSearch subscription levels. Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/auditing-settings.html |
| elasticsearch_ssl_diagnose_trust_true | 4 | ElasticSearch has a setting to log diagnostic messages for SSL/TLS trust failures. The default for this setting is dependent on other settings, and hence should be explicitly set to true. Remediation: Ensure the setting xpack.security.ssl.diagnose.trust is set to true explicitly (ambiguous default).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| elasticsearch_slm_allowed_urls | 4 | ElasticSearch allows to configure specific URLs from which snapshots can be restored. This setting should be set to ensure that snapshots are not randomly retrieved Remediation: Ensure the setting repositories.url.allowed_urls is set to any value.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/slm-settings.html |
| elasticsearch_destruction_requires_name | 4 | You may be able to delete all indices in an ElasticSearch cluster at once by issuing a call likeDELETE /_all. To allow something like this to happen by accident is not advisable. To prevent accidental large deletions, one should specifically set that indices can only be deleted by name.Remediation: Set the value action.destructive_requires_name to true explicitly.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/index-management-settings.html |
| dockerfile_create_volume_for_var_log | 3 | In linux systems, important operating system logs are stored in the /var/log subfolder. This folder should always be made available to the host through a volume, so that log tracking and log analysis systems can capture them. Remediation: In every Dockerfile, there should be a VOLUME directive which has /var/log as an argument.Source: https://docs.docker.com/engine/reference/builder/ |
| elasticsearch_memlock_all | 3 | ElasticSearch's performance is largely due to in-memory operations. This performance is often hindered by the garbage collection of the JVM, which may swap some pages of the heap to disk. One way to prevent that and increase general performance of your ElasticSearch cluster is to request the JVM to lock the heap memory via mlockall (Unix) or virtual lock (Windows).Remark 1: It is possible that the operating system layer may prevent this command, so you need to check if it is really active on the specific host after running it. Remark 2: Ensure that the ElasticSearch process is given enough heap space by the JVM to support any load your organization may put on it. Remediation: Ensure the setting bootstrap.memory_lock is set to true (default: false).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/_memory_lock_check.html |
| elasticsearch_enable_fips | 3 | There is a setting in ElasticSearch to explicitly enable the standards set by the Federal Information Processing Standard (FIPS). This should be enabled to comply with latest security standards. Remediation: Set xpack.security.fips_mode.enabled to true (default false).Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/security-settings.html |
| dockerfile_copy_command_more_than_two_arguments_slash | 2 | The COPY directive allows the copying of one or more files on the host machine into the image that is being built. If there is more than one file copied, it is apparent that the destination is a folder, and hence has to end with /. Remediation: Ensure that every COPY instruction with more than two arguments has the last argument ending with /Source: https://docs.docker.com/engine/reference/builder/#copy |
| dockerfile_container_healthcheck_parameter | 2 | Dockerfiles have an instruction called HEALTHCHECK. It enables a user to define a command to figure out if the program(s) running inside the container are working properly. It is generally advisable to have healthchecks in place to assist monitoring of running containers. Remediation: Have at least one HEALTHCHECK instruction in your Dockerfile.Source: https://docs.docker.com/engine/reference/builder/#healthcheck |
| elasticsearch_reindex_remote_whitelist_not_arbitrary | 2 | ElasticSearch allows re-indexing from remote locations. These should be well defined, and are currently defaulting to [["*.io:", "*.com:"].] Remediation: Set the value reindex.remote.whitelist to values that are specific sites with no wildcards.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/index-management-settings.html |
| elasticsearch_seed_hosts_set | 2 | ElasticSearch allows to configure an initial list of master-eligible nodes on the cluster. By default, a node will consider itself a master as well. It is important to design the cluster with master nodes in mind and set them initially. Remediation: Set the discovery.seed_hosts in your configuration, containing your chosen hosts.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/modules-discovery-settings.html |
| dockerfile_env_and_arg_defined_and_right_away_used | 1 | When creating Docker images that use environment variables or build arguments, it is advisable to position the ARG or ENV directives close to their actual uses, since otherwise the caching for building the images is not greatly used.Remediation: Every variable defined by an ENV or ARG directive should be used within the next five commands inside the Dockerfile. |
| elasticsearch_index_refresh_interval_set | 1 | ElasticSearch periodically refreshes indices that have been operated on. This refresh is a resource intensive operation, and hence the operator of the ES cluster should evaluate how large the real-time needs of the ES cluster are and consider potentially larger refresh intervals. Remediation: Ensure the setting index.refresh_interval is set to an explicit value (non-default) to show that the administrator has given it consideration.Source: https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules.html#index-refresh-interval-setting |
Scan performed at 2022-12-12 15:23:07 using the CoGuard CLI