Docker Image Scan results for vmware/postgresql-photon
Scan performed at 2022-12-12 15:23:07 using the CoGuard CLI
Summary
14 Total failed checks.
3 High / 1 Medium / 10 Low.
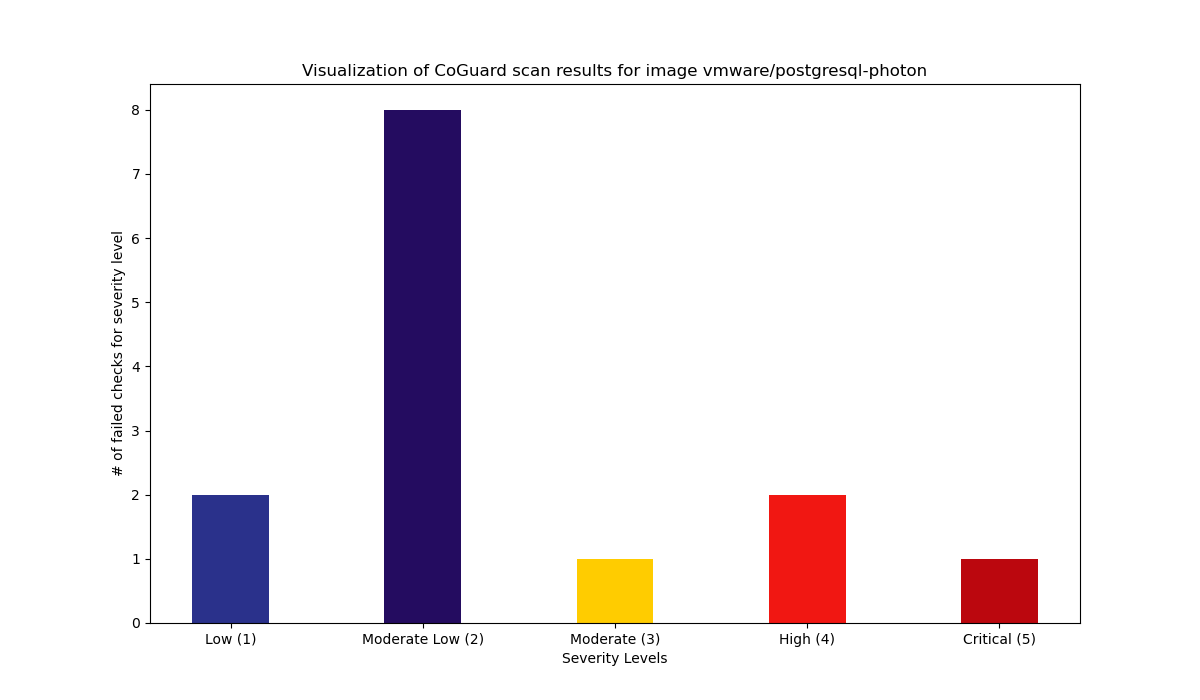
Details
| Rule identifier | Severity | Documentation |
|---|---|---|
| postgres_enable_ssl_traffic | 5 | The communication to the database should always be encrypted. Remediation: Set the ssl directive to on.Source: https://www.postgresql.org/docs/current/ssl-tcp.html |
| postgres_enable_archive_mode | 4 | In order to perform point in time recovery, the archive mode in Postgres needs to be set to be on. Remediation: Set the directive archive_mode to on.Source: https://wiki.postgresql.org/wiki/Simple_Configuration_Recommendation |
| dockerfile_last_user_should_be_non_root | 4 | When creating a Docker container, it is possible to set the user who is actually running the application and any command on the container. It is important to specifically use the USER directive in any Dockerfile to ensure that the user is not root and has unnecessary privileges. Remediation: Have at least one USER directive in your Dockerfile, and the last user directive should not reference the root user or root group. Source: https://docs.docker.com/engine/reference/builder/#user |
| dockerfile_create_volume_for_var_log | 3 | In linux systems, important operating system logs are stored in the /var/log subfolder. This folder should always be made available to the host through a volume, so that log tracking and log analysis systems can capture them. Remediation: In every Dockerfile, there should be a VOLUME directive which has /var/log as an argument.Source: https://docs.docker.com/engine/reference/builder/ |
| kerberos_only_one_kdc | 2 | A KDC can have multiple backup KDCs, which is recommended, because otherwise everyone is locked out if the Kerberos machine goes down. Source: http://web.mit.edu/kerberos/krb5-devel/doc/admin/install_kdc.html |
| postgres_enable_logging_connections | 2 | Postgresql offers a mechanism to log connections to the database. This is recommended to be turned on, as it enables the system administrator to analyze these logs and detect anomalies. Remediation: Set the directive log_connections to on.Source: https://wiki.postgresql.org/wiki/Simple_Configuration_Recommendation |
| postgres_enable_logging_disconnections | 2 | Postgresql offers a mechanism to log ends of sessions, including the duration of sessions. This is recommended to be turned on, as it enables the system administrator to analyze these logs and detect anomalies. Remediation: Set log_disconnections to onSource: https://www.postgresql.org/docs/9.1/runtime-config-logging.html |
| postgres_ensure_log_directory_is_set | 2 | Postgres allows you to set your own log directory, which in turn ensures that the user as which Postgresql is run is allowed to write into that directory. It is recommended to set this directory specifically. Remediation: Set log_directory to a value of your choice.Source: https://www.postgresql.org/docs/10/runtime-config-logging.html |
| postgres_ensure_log_rotation_size_not_disabled | 2 | Log file rotation by by size is part of logging best practices. It is important to have a value set there that follows your companie's policies Remediation: Set the parameter log_rotation_size to any value other than 0Source: https://www.postgresql.org/docs/10/runtime-config-logging.html |
| postgres_do_not_use_standard_port | 2 | Using the standard port makes it easier for intruders to scan for the service from the outside Remediation: Set the parameter port to any other value than 5432 |
| postgres_log_timezone_utc | 2 | Working in different timezones is a great area of error. For logging, it is generally recommended to use UTC time, and convert in visual tools to local times as needed. By default, Postgres uses the operating system's timezone setting as its timezone for logging. It is best to set it to UTC to avoid confusion, or to your organization's standard time zone setting. Remediation: Set the parameter log_timezone to UTCSource: https://www.postgresql.org/docs/10/runtime-config-logging.html |
| postgres_log_statement_not_none | 2 | By default, log statements are not logged at all. It is useful for auditing purposes to at least set it to ddl, meaning that DROP, ALTER and CREATE statements are being logged.Remediation: Set the parameter log_statement to anything other but none (default value is none).Source: https://www.postgresql.org/docs/10/runtime-config-logging.html |
| dockerfile_env_and_arg_defined_and_right_away_used | 1 | When creating Docker images that use environment variables or build arguments, it is advisable to position the ARG or ENV directives close to their actual uses, since otherwise the caching for building the images is not greatly used.Remediation: Every variable defined by an ENV or ARG directive should be used within the next five commands inside the Dockerfile. |
| dockerfile_do_not_use_add | 1 | Dockerfiles have two directives that allow you to add files from the machine where you build the image into the image, namely COPY and ADD. Both are technically similar, but ADD also has side-effects like automated decompression of archives. It is generally recommended to only use COPY Remediation: Remove any ADD directive in your dockerfile and replace it with COPY.Source: https://docs.docker.com/engine/reference/builder/#copy |
Scan performed at 2022-12-12 15:23:07 using the CoGuard CLI