Docker Image Scan results for ibmcom/kafka-java-liberty-sample
Scan performed at 2022-12-12 15:23:07 using the CoGuard CLI
Summary
57 Total failed checks.
30 High / 21 Medium / 6 Low.
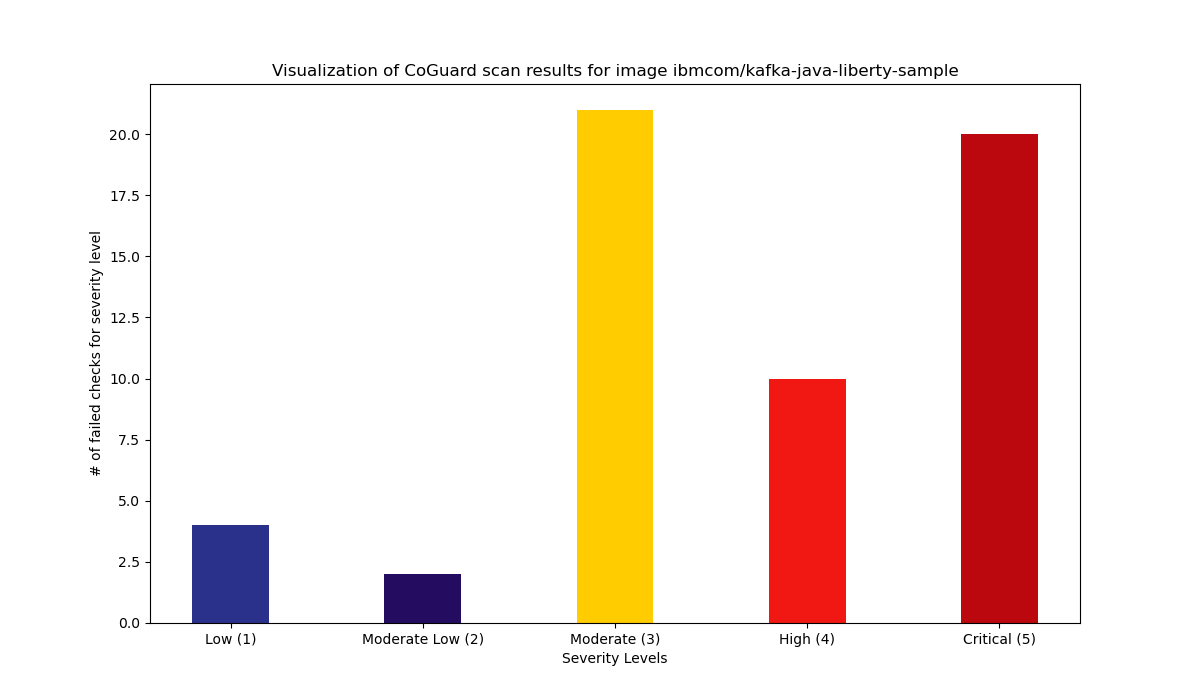
Details
| Rule identifier | Severity | Documentation |
|---|---|---|
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_disable_shutdown_port | 5 | Tomcat, by default, listens on port 8005 for messages with a shutdown request. The message by default is SHUTDOWN, which of course could be probed. One should change this value to a random one not known to attackers, if one is not disabling the shutdown port explicitly.Remediation: Ensure that in the server.xml file, inside the Server tag, the attribute shutdown attribute is set to anything but SHUTDOWN.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/server.html |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_let_root_start_tomcat | 5 | There is a way to ensure that Tomcat is not started by the root user, which would give it root-privileges. Remediation: In the server.xml, ensure that a Listener tag is present, with the attribute className being org.apache.catalina.security.SecurityListener and root not being part of the comma separated list in the attribute checkedOsUsers (default is root).Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#Security_Lifecycle_Listener_-_org.apache.catalina.security.SecurityListener |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_do_not_have_compression_enabled | 4 | Compression and encryption in combination results in being a risk for the well-known BREACH attack. Since we always recommend to encrypt all your traffic, you need to turn compression off. Remediation: Ensure in the server.xml file that any Connector instance does have the attribute compression set to off (default is off).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_remove_x_powered_by_header | 3 | The lesser anyone connecting to the server knows about the underlying architecture, the better. Any connector can be instructed to have an X-Powered-By header, which should be avoided in any case. Remediation: Ensure in the server.xml file that any Connector instance does not have the attribute xpoweredBy set to true (default is false).Source: https://tomcat.apache.org/tomcat-9.0-doc/security-howto.html#Connectors |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| tomcat_enable_memory_leak_listener | 3 | Memory leaks are among the main causes of server performance degradation. It is important to catch them and provide work-arounds. Remediation: In the server.xml, ensure that the following line is present: <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" />.Source: https://tomcat.apache.org/tomcat-9.0-doc/config/listeners.html#JRE_Memory_Leak_Prevention_Listener_-_org.apache.catalina.core.JreMemoryLeakPreventionListener |
| dockerfile_create_volume_for_var_log | 3 | In linux systems, important operating system logs are stored in the /var/log subfolder. This folder should always be made available to the host through a volume, so that log tracking and log analysis systems can capture them. Remediation: In every Dockerfile, there should be a VOLUME directive which has /var/log as an argument.Source: https://docs.docker.com/engine/reference/builder/ |
| dockerfile_only_one_cmd_instruction | 2 | The CMD directive specifies the final command that is executed when running the container. This should be unique. Remediation: Ensure that there is at most one CMD directive in the Dockerfile. |
| dockerfile_container_healthcheck_parameter | 2 | Dockerfiles have an instruction called HEALTHCHECK. It enables a user to define a command to figure out if the program(s) running inside the container are working properly. It is generally advisable to have healthchecks in place to assist monitoring of running containers. Remediation: Have at least one HEALTHCHECK instruction in your Dockerfile.Source: https://docs.docker.com/engine/reference/builder/#healthcheck |
| dockerfile_env_and_arg_defined_and_right_away_used | 1 | When creating Docker images that use environment variables or build arguments, it is advisable to position the ARG or ENV directives close to their actual uses, since otherwise the caching for building the images is not greatly used.Remediation: Every variable defined by an ENV or ARG directive should be used within the next five commands inside the Dockerfile. |
| dockerfile_only_one_definition_per_env_statement | 1 | The ENV statement allows multiple definitions. This should be avoided for readability reasons, as well as pitfalls like variables not being evaluated if defined within the same ENV directive. Remediation: Ensure that every ENV directive has only one assignment. |
| dockerfile_do_not_use_maintainer | 1 | Dockerfiles allow for a specification of a MAINTAINER. This directive is deprecated, and should generally be replaced with the LABEL directive. Remediation: Remove any MAINTAINER directive in your Dockerfile and replace it with LABEL.Source: https://docs.docker.com/engine/reference/builder/#maintainer-deprecated |
| dockerfile_do_not_use_add | 1 | Dockerfiles have two directives that allow you to add files from the machine where you build the image into the image, namely COPY and ADD. Both are technically similar, but ADD also has side-effects like automated decompression of archives. It is generally recommended to only use COPY Remediation: Remove any ADD directive in your dockerfile and replace it with COPY.Source: https://docs.docker.com/engine/reference/builder/#copy |
Scan performed at 2022-12-12 15:23:07 using the CoGuard CLI